CHAPTER 5
l Digital Security Risks
Digital security risks any event or action that could cause a loss of or damage to a computer or mobile device hardware, software, data, information, or processing capability.
Computer crime any illegal act involving the use of a computer or related devices generally is referred to
Cybercrime is an online or Internet-based illegal act
 |
| HACKERS @ CRACKER |
 |
| CORPORATE SPIES |
 |
| UNETHICAL EMPLOYEE |
Hackers
|
Crackers
|
1.Break the computer system with
ethics to test the weakness of the system.
2. Do not damage the system or destroy data.
|
1. Deliberately breaks the system
to bring damageand sabotage
elements.
2. Unethical.
3. Aggressive and dangerous
|
l Internet and Network Attacks
Malware, short for malicious software, consists of programs that act
without a user’s knowledge and deliberately alter the operations of computers
a mobile devices
without a user’s knowledge and deliberately alter the operations of computers
a mobile devices
Firewall is hardware and/or software that protects a network’s resources from intrusion
l Unauthorized Access and Use
Unauthorized access is the use of a computer or network without permission
Unauthorized use is the use of a computer or its data for unapproved or
possibly illegal activities
possibly illegal activities
The computer, device, or network should maintain an audit trail that
records in a file both successful and unsuccessful access attempts
records in a file both successful and unsuccessful access attempts
ü User name
ü Password
ü Password
ü Passphrase
ü CAPTCHA
ü Fingerprint reader
ü Face recognition system
ü Hand geometry system
ü Voice verification system
ü Iris recognition system
ü Signature verification system
A possessed object is any item that you must carry to gain access to a computer or computer facility
Often are used in combination with a PIN (personal identification number)
A biometric device authenticates a person’s identity by translating a personal
characteristic into a digital code that is compared with a digital code in a computer
characteristic into a digital code that is compared with a digital code in a computer

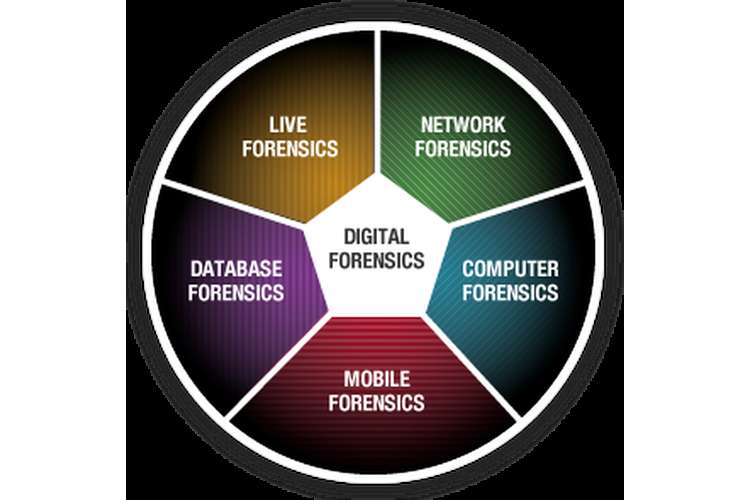
Digital forensics is the discovery, collection, and analysis of evidence found on
computers and networks
computers and networks
l Software Theft
Software theft occurs when someone:
Steals software media
|
Intentionally erases
programs |
Illegally registers and/or activates
a program |
Illegally copies a program
|
v A digital signature is an encrypted code that a person, website, or
organization attaches to an electronic message to verify the identity of the
sender
organization attaches to an electronic message to verify the identity of the
sender
v Often used to ensure that an impostor is not participating in an Internet
transaction
transaction
v A digital certificate is a notice that guarantees a user or a website is
legitimate
legitimate
v A website that uses encryption techniques to secure its data is known as a
secure site
secure site
l Hardware Theft, Vandalism, and Failure
v Hardware theft is the act of stealing digital equipment
v Hardware vandalism is the act of defacing or destroying digital equipment
l Backing Up – The Ultimate Safeguard
Backup is a duplicate of a file, program, or media that can be used if the original is lost, damaged, or destroyed
To back up a file means to make a copy of it
Off-site backups are stored in a location separate from the computer or mobile device site
l Ethics and Society

l Information Privacy
Information privacy refers to the right of individuals and companies to deny or restrict the collection and use of information about them
v Phishing is a scam in which a perpetrator sends an official looking email message that attempts to obtain your personal and/or financial
information
information
v With clickjacking, an object that can be clicked on a website contains a
malicious program
malicious program
v Spyware is a program placed on a computer or mobile device without the user’s knowledge that secretly collects information about the user and
then communicates the information it collects to some outside source
while the user is online
then communicates the information it collects to some outside source
while the user is online
v Adware is a program that displays an online advertisement in a banner or pop-up window on webpages, email messages, or other Internet services


Comments
Post a Comment